DownUnder CTF (DUCTF) 2023
·2 mins

Table of Contents
Introduction #
- Last weekend, I took part in the DownUnder CTF alongside my team Fr334ks-Mini and this is the write-up for the challenges that I solved.
1. Discord #
Category: Misc
Difficulty: Beginner
- We are given a file
message.txt. - We download the file and open it
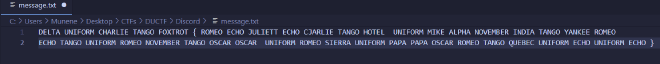
- We can see that the flag is made from picking the first letter of every word so our flag will be: DUCTF{REJECTHUMANITYRETURNTOOURSUPPORTQUEUE}
2. Static File Server #
Challenge Description #
Accessing the Web Server #
- On accessing the web server we are presented with the following web page
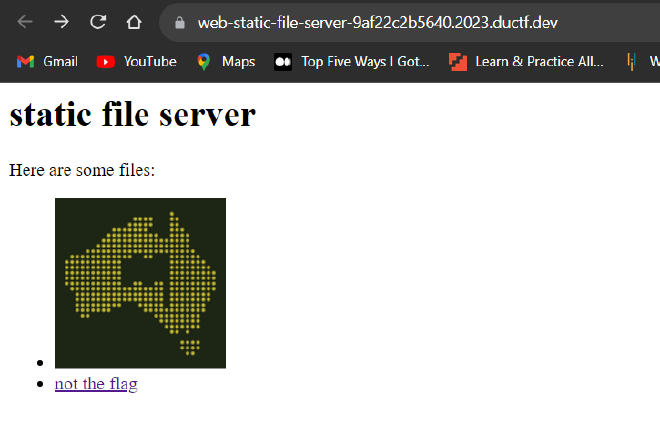
- We can see that there is a hyperlink
not_the_flagbelow the image in the page. It’s a good idea to have a look at it first and see where it takes us.
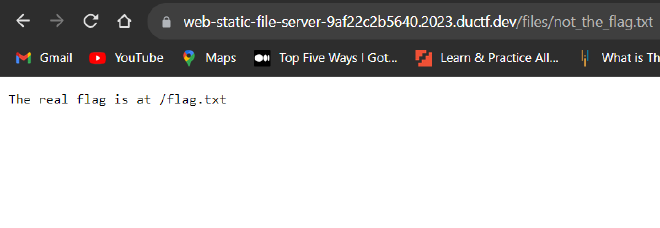
- Clicking on the link serves us with a
.txtfile that tells us that the real flag is at/flag.txtAttempting to access/flag.txtled me to a dead end with the errorNot Found
Web Directory Listing #
Let’s see whether we can list the directories and files in the server. We can use
curlcommand for that.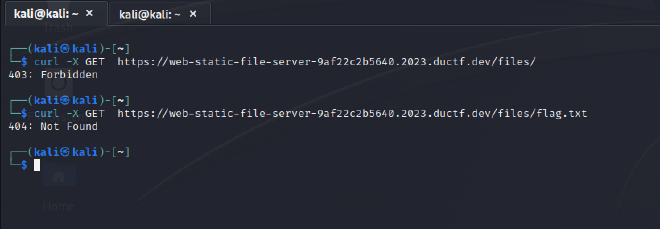
Attempting to access
/filesreturns a403: Forbiddenand attempting to access/files/flag.txtreturns a404: Not Found.Given the 403 Error let’s attempt a directory traversal and see whether the app is vulnerable.
Analysis Using Burp Suite #
- sending
/files/../../../../flag.txtpayload … Guess what?! The reponse contains the flag :)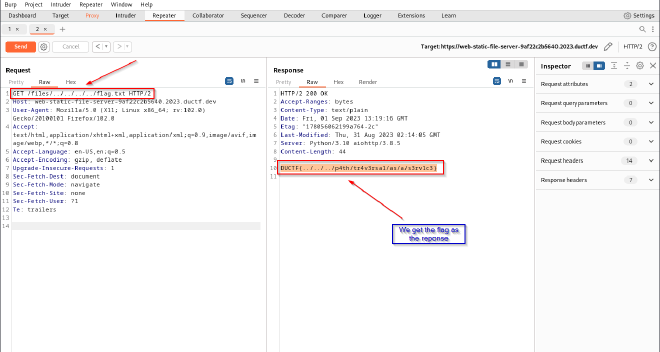
Conclusion #
- I enjoyed solving this challenge! See you in the next blog :)